A recording will be available to registered participants, in case they are not able to attend all the live sessions.
For more information or questions, please contact: training@veranex.com
Training Objectives
This training is organized into different modules with the goal of providing participants with an extended understanding of requirements related to medical device software cybersecurity. Individual modules link key regulatory and technical consideration related to developing secure medical device software, with a specific focus on cybersecurity requirements. The training is aimed at any software engineer, product manager, regulatory affairs specialist, or regulatory manager seeking to enhance their competence in this rapidly developing domain.
Participants can select from the following three programs:
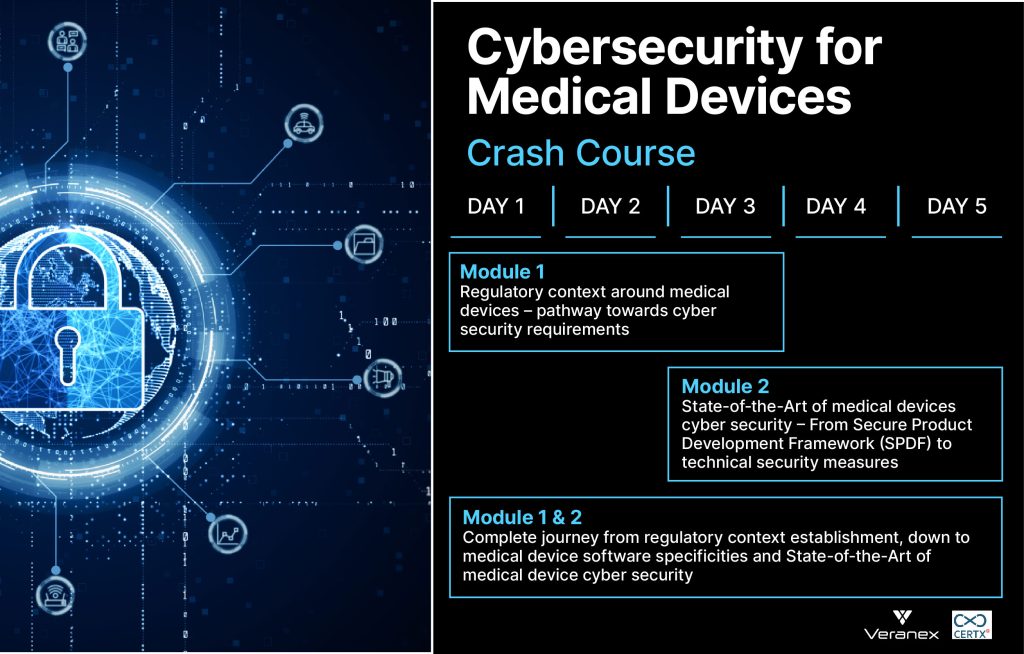
- Module 1: Regulatory context around medical devices – pathway towards cybersecurity requirements
- Module 2: State-of-the-Art of medical devices cybersecurity – From Secure Product Development Framework (SPDF) to technical security measures
- Module 1&2: Complete journey from regulatory context establishment, down to medical device software specificities and State-of-the-Art of medical device cybersecurity
Training Content
Day 1: Key requirements for marketing medical device software
- Is my software in scope of EU medical device regulations (MDR & IVDR)?
- How do I classify my software under the EU medical device regulations (MDR & IVDR)?
- How is cybersecurity linked with regulatory requirements?
- Which guidance and standards can help me meet these requirements?
- What are cybersecurity terminology related to medical device software?
Day 2: Cybersecurity concepts – Life cycle management for medical device software and information security
IEC 62304: Medical device software – Software life cycle processes
- How do I develop medical device software within a quality management system?
- What is Software Safety Classification under IEC 62304?
- How do I develop a verification and validation plan for my software?
- How do I manage vulnerabilities within the risk management process?
- How do I test cybersecurity requirements?
IEC 27001: Information Security Management Systems
- What is information security?
- How is information security linked with cybersecurity?
Day 3: From regulatory requirements for medical devices towards cybersecurity enforcement
- What are the key steps to ensure compliance with cybersecurity requirements for my CE Mark
- How do I generate and organize technical documentation?
- What is the IEC 62443 certification scheme and why should I pursue it?
- New cybersecurity standard tailored for medical devices ( IS0/IEC 80001-5-1 – IEC TR 60601-4-5)
- What shall I present to my notified body during a CE Mark conformity assessment process?
- How do I leverage my Post Market Surveillance process to further demonstrate compliance on my CE Marked software?
Day 4: Secure Product Development Framework (SPDF) – Cybersecurity practices for developing & maintaining secure products – IS0/IEC 80001-5-1
- Cybersecurity perimeters – IT, OT, product cybersecurity
- Cybersecurity standards, norms and guidelines
- Product cybersecurity lifecycle overview, organization
- Product cybersecurity across supply chain
- Product cybersecurity development phase, incl. cyber risk assessment
- Product cybersecurity post-development phase & post-market surveillance
Day 5: Introduction about technical security measures and State-of-the-Art of cybersecurity technologies
- Introduction to cybersecurity primitives and algorithms
- Product cybersecurity technologies and architecture landscape
- ISA/IEC 62443-4-2/ IEC TR 60601-4-5 as a standardized catalogue for technical component security capabilities
- Product cybersecurity threat model & risk assessment – use case example
Training Format
- Presentation with interactive discussions
- Exercises during the training
- End-of-training assessment (participants will receive a training certificate)
Who Should Attend
- Software engineers
- Product managers
- Regulatory affairs specialists or regulatory manager
Prerequisites
- Participants shall have an understanding on medical device regulatory landscape in EU and on Quality Management System (QMS).
- Basic knowledge on IEC 62304 is desired.
Price
Module 1: 750 EUR
Module 2: 750 EUR
Module 1&2: 1’200 EUR
The training is a partnership between CertX and Veranex. The training will be delivered online through 5 sessions of approximately 4 hours each during a week-long intensive training. The training is scheduled to take place from November 4th to 8th. A recording will be available to registered participants, in case they are not able to attend all the live sessions. A training certificate will be provided to participants.
